Protect and Secure Your Customer’s Information
IMS Security Experts Share 3 Tips on How You Can Protect and Keep Your Sensitive Customer Data Safe
In recent years the insurance and automotive industry have seen significant growth in the area of telematics and connected car services. With an estimated 250 million connected cars expected on the road by 2020, the connected car presents a great opportunity for the automotive market with several business opportunities in key areas such as usage-based insurance (UBI), fleet management and road charging. These opportunities provide benefits to the companies delivering the programs and the drivers taking advantage of them.
With connected car technology at the forefront of the automotive industry news, questions are arising in relation to potential security risks associated with them. As is common with any new technology, the increasing prevalence and availability have led to increased media accounts about how having an OBD II device, for example, can leave you vulnerable to hacking, compromising the security of the information being collected, and posing a threat to the driver and the vehicle. Many consumers are being led to believe that the devices they are plugging into their cars are easily manipulated and can be hacked to steal personal information or to hijack the cars’ computer system.
So how does a customer ensure that their security needs are being met when considering a telematics program or enabling connected car services via smartphones or tablets? And what can an organization do to reassure the end-user that all precautions are being taken against the hijacking of information and device tampering?
Here are 3 tips companies adopting a connected car solution need to ensure, most importantly the service provider they choose meet security requirements in the same way they would if they were developing and deploying the solution internally. IT personnel need to be able to make an educated decision and consider the following to ensure security, availability and data integrity:
1. End-to-End Security: The security and data privacy is core to successful automotive telematics. The organization chosen should be an expert in network security and infrastructure. Security measures need to be in place at every access point to prevent unauthorized access.
Below is an example of the IMS End-to-End Data Security Implementation where the carrier network communicates with the IMS security infrastructure via a VPN tunnel. In addition, the data is encrypted using 256-bit AES encryption. At this point, there is a very secure path from the device to the IMS systems.
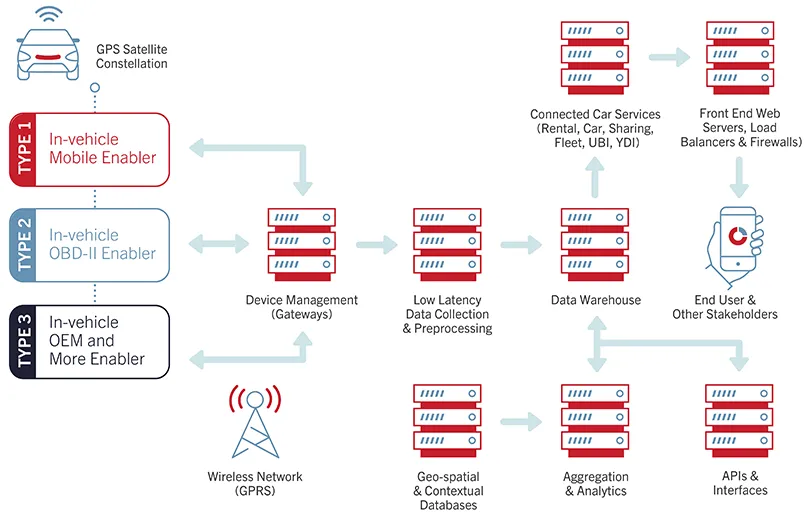
2. Data Collection Integrity: It is very important to ensure that the data collected from vehicles is retained in its raw state, so if data corruption occurs, the original data can be restored. Data that is collected needs to not only be protected but need to maintain its integrity.
3. Information Availability: All systems should be built to ensure high information availability and scalability. Systems should be actively monitored to maintain health and a high level of service without interruption.
The strategies outlined above are only some of the measures you can take to improve the connected car security needs of your customers. CIOs and security executives should look for service providers who can deliver a highly secure, scalable, and highly available environment. A good example of this is the production environment at IMS which has been built to ensure high information availability and scalability. IMS production systems are hosted at a CICA 5970 and SSAE (Type II) certified hosting facility within Canada. The facility is engineered to deliver 99.999% availability, featuring redundant power, cooling, and network infrastructure.
IMS has been delivering connected car solutions since 1999, and delivers a high-value telematics-based platform which delivers end-to-end security, data collection integrity, and information availability. IT decision-makers can feel confident that IMS has the technology, processes, and people to make telematics programs successful within their organizations.
Download IMS Connected Car And Telematics Data Security White Paper >

